- Bitvise Ssh Client Windows
- Bitvise Ssh Client 8.37 Download
- Bitvise Ssh Client Portable
- Bitvise Ssh Client Macos Os
- Download Bitvise Ssh Client
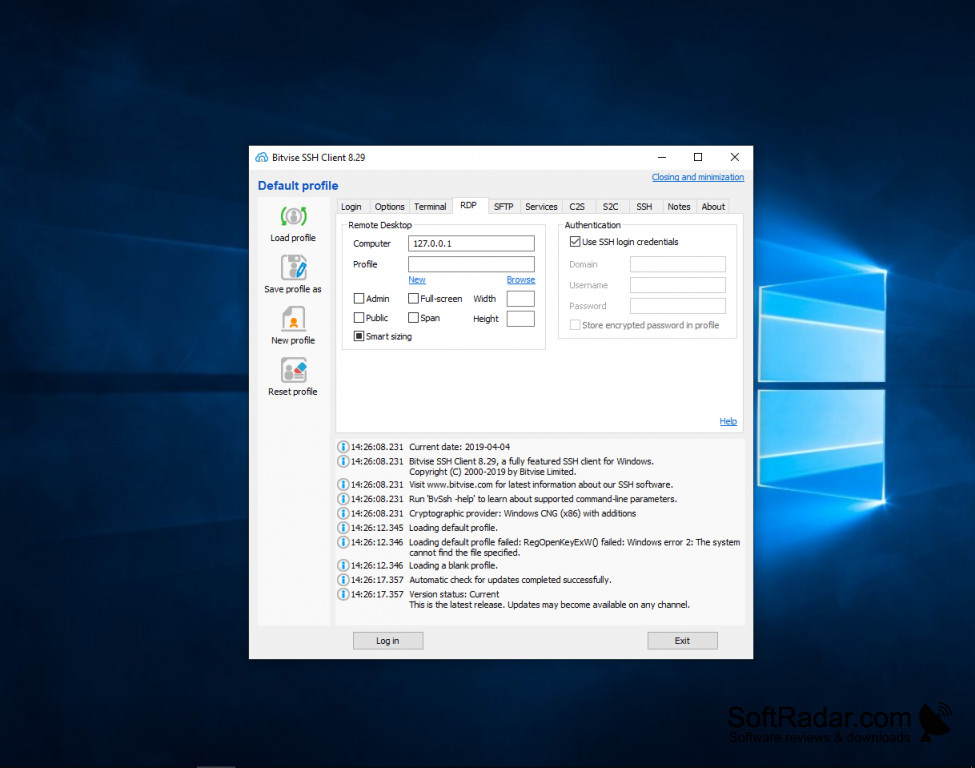
PuTTy is probably the SSH client used the most on Windows. It’s a portable free tool that supports not only SSH but Telnet, Xterm as well. It’s also a simple and easy-to-use tool as well. Simply put in the hostname and click Load button to start. Bitvise offers both SSH Server and SSH Client for Windows Servers and workstations.
- 01 – Solar-PuTTY Windows. Manage remote sessions in a professional way. Connect to any server.
- FIPS 140-2 validation: Bitvise SSH Client 6.xx uses the FIPS-certified DLL version of Crypto 5.3.0, originally validated by NIST under certificate #819.
Important
On 2020/10/01, the CS department changed host keys to strengthen security.
Bitvise Ssh Client Windows
The CS IT staff has recently updated the SSH subsystems. This update will havean effect on the SSH client used to connect to the CS systems, includingOpenStack virtual machines and the multilab systems. The previous method of hostidentification is outdated and less secure than newer methods (we are now usinged25519 changing from rsa).
SSH uses a process of identification using keys, much like the ones used to identifywebsites that you connect to using “https”. When the key that is used toidentify the computer changes the SSH client sees that the identification haschanged and will issue a warning.
These warnings are rare and should cause concern when they are presented. If youare presented with one of these messages indicating the remote hostidentification has changed and are concerned about it, please contact us athelp@cs.uky.edu.
Terminal Connections¶
When you connect via a terminal to a Computer Science machine you may bepresented with a message similar to the one below:
or
Removing old keys¶
If your SSH client supports it you can run the command indicated in thesecond message from above.
Some SSH clients do not support removing keys with ssh-keygen, on those systemsyou will need to manually edit the ‘known_hosts’ file. The exact line with theoffending key is indicated in the above message like this `OffendingRSAkeyin/path/to/home/username/.ssh/known_hosts:35` which indicates the key is online 35 of ‘known_hosts’. Edit the file, removing line 35, and save it.Performing one of the above methods will allow your client to get the new keyand connect successfully to the remote host.
Bitvise, Putty, & Others¶

GUI SSH clients will have a pop-up prompt with either an informational messageindicating the host has a new key or an indication that a new key was presentedto the client. In all the GUI applications tested there is a button located onthis pop-up which allows you to accept the new key and store it in the clientscache.
Bitvise Ssh Client 8.37 Download
Putty - New host key pop-up
If you run into any error like the one below, indicating key exchange alogrithm(or cypher) could not be agreeed on or negotiated you will need to upgrade yourclient.
To download an updated client for Putty, go here: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
For Bitvise, go here: https://www.bitvise.com/download-area
Here are some other common SSH Clients:
Our vulnerability reports show that our Macs are running OpenSSH 7.9 and need to be updated to 8.1. The OS is Mojave. This doesn't seem to be as straight forward as on A PC. Any ideas on how this is done?
First thing to note is that ssh is not enabled by default on any install of OS X (excluding server, which is a now-dead version, as a separate build and customizations of OS X).
Upgrading is easy, use MacPorts (many will without question suggest homebrew, I prefer and recommend MacPorts based on historical - personal - experience).
Bitvise Ssh Client Portable
https://ports.macports.org/port/openssh/summary
Bitvise Ssh Client Macos Os
One would have to modify
/System/Library/LaunchDaemons/ssh.plist
Download Bitvise Ssh Client
to use said upgraded ssh (which will get installed via MacPorts - by default - to /opt/local ), which is no small task especially for Mojave, in which /System is protected by SIP.No-one with a meaningful knowledge of security and macOS (Mac OS X) will recommend disabling SIP. One might be able to do so temporarily, but that's another hill to climb/problem to solve.
Technically, you could leave the default installed openssh alone, but that will still get used when using the macOS GUI (System Preferences > Sharing) to enable ssh ('Remote Login'), unless you managed to edit the above-named plist to point to your updated version.